The most common reason to information leakage is basically human mistakes!
Different kind of data Loss Prevention (DLP)-solutions can be helpful to assist our users to follow the company guidelines around information handling. Microsoft have just announced their new Endpoint DLP as General Available!
Endpoint DLP can be useful in several scenarios. It can be used to alert on different actions, both for end-users as well as the admins. It can also be used to prevent or warn the end-user , this can be really helpful in educational purposes. Increasing the knowledge of information management among our users can often be the best protection for our information.
A common business requirement that I have heard of (mostly from organizations in the public sector) is that some information is not allowed to be stored in a cloud service. A combination of Conditional Access (that limit the access only for managed devices) and Endpoint DLP for these cloud services can be used to meet these needs.
But let us have a look how to configure this in the compliance portal.
When we create a DLP policy we define what kind of location this is for.
Endpoint DLP is for our devices and works (today) for Windows 10. We can easily test this for a small amount of users by defining this policy per user or group.
We can then create rules with conditions for certain information based on:
- Included information types (everything from predefined types like credit cards, personal ID´s to custom information types)
- Sensitivity of the information based on its Sensitivity label
We can also exclude content based on the same two options (information type/label) if there is a need for that.
When these conditions are met, we can then decide what we want to do around these types of actions. We can choose to
- only audit the specific action
- block the action with the possibility for the end-user to override
- Block the action
The above activities:
- Upload to cloud services or access by unallowed browsers
- Access by unallowed apps
are based on central configured EndPoint DLP settings.
Here we can for instance add our unallowed apps. In this business case we had a specific label that was not allowed to be stored in Office 365, therefor we had to add Microsoft Teams as an unallowed app. Other unallowed apps could be different sync agents for instance the DropBox, Itunes and OneDrive that could prevent syncing the relevant classified information.
The end-user experience for a blocked app will be like this:
To be able to restrict uploading of content to different web services we must exclude browsers that does not support Endpoint DLP. Notice that we do not stop these browsers (or specified unallowed apps) to run, we just block them to be used with certain information, defined by our DLP rules.
Endpoint DLP with Microsoft Edge.
For our restrictions to either “block” or “block with override” for uploading to defined cloud services, this is based on central DLP Settings. This function requires the Microsoft Edge browser
We can run this in a black- or whitelist scenario where we can either allow defined domains and block all the rest or we can choose to block defined domains.
In my business case where a specific label was not allowed to be stored in Office 365 (or Google) we defined the domains for these services.
The end-user experience for a block with override policy for a defined domain will be like this: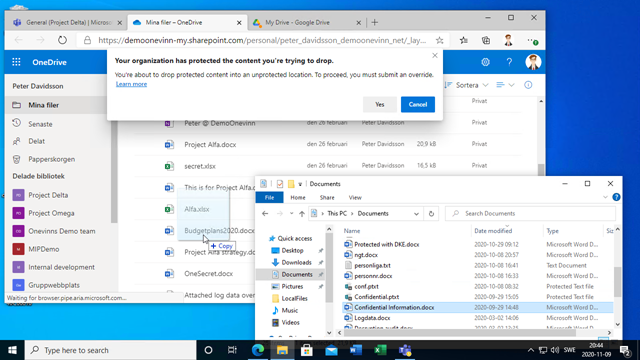
Regardless if the action is to block our just Audit specified action, we can define different notification options (per policy). If we want to notify the user or somebody else in the organization, we can do this by email.
We can also trigger an incident report and define what kind of sensitivity the specific incident should have.
An important take around DLP is that as soon as you block the user from something, you need to have an answer to how they should solve the business need instead. If you block too much there is always a risk that your users will use another (unsanctioned) service to do their work. In that case you will lose control completely and will have what is called a Shadow IT.











